As part of the merger and acquisition (M&A) due diligence process, every company must consider supply chain risk.
The entire supply chain — supplier, vendor, customer, labor, third parties, etc. — is fraught with potential risk that can ladder up to an enormously adverse impact for the consolidating firms and investors. This makes corporate governance and risk mitigation instrumental to supply chain transparency and responsible business conduct.
Within the context of an M&A, business leaders often face myriad supply chain due diligence questions. We’ll examine several critical questions, using a hypothetical firm.
Why Supply Chain Matters to the M&A Process
Supply chain risks typically derive from third-party suppliers (e.g., “raw material” providers many manufacturers depend on, a piece of third-party software on your systems, or a third-party hosted system in their cloud). Whoever they are, third parties provide products or services businesses rely on for operation.
Third parties introduce a wide variety of risks to an organization, which need to be planned for. These risks are generally unique to individual third parties, but one factor is universal: They can have devastating consequences to your organization’s reputation and bottom line.
Suppliers provide several avenues for attackers to access your network and data or disrupt your organization. There are two main scenarios:
- Loss of service for critical applications and services
- Loss of proprietary data, whether from customers, employees, or other third parties.
Both pose serious consequences to an organization.
Consider the following fictitious example of an acquisition gone wrong:
Ajax Software was a start-up rising star in the e-commerce world. They created a solution that took the internet payments world by storm. Recognizing their growth and the need to expand operations, the owners sought a strategic partner to help grow their business. Attracted by Ajax’s existing market share and recognizing the synergy with their current web-based business, MegaWeb Corporation presented Ajax an acquisition offer. Owners of both companies agreed on the terms.
Prior to the acquisition, the secret to Ajax Software’s success was their proprietary, home-grown software platform and its simple integration with customer websites. With the acquisition complete, MegaWeb Corporation realized integrating Ajax’s systems into theirs would be the most effective way to help both companies scale and beat competitors.
Due to management, investor, and market pressures, MegaWeb Corporation conducted a shortened due diligence process to speed the acquisition. The next release of Ajax’s platform would bring much-requested features and address a market on which they wanted to rapidly capitalize. The acquisition process was completed, and the “Mega-Ajax” platform was released to great fanfare and success.
A year after the acquisition, a national news site published a story with headlines identifying Mega-Ajax as a victim of EvilX, an international crime syndicate that compromised Mega-Ajax’s customer account database and corporate systems. In the days and weeks following the article, customers reported their identities and credit card information had been stolen. Worse still, as Mega-Ajax began to respond to these claims, their corporate systems were shut down by a devastating ransomware attack.
Faced with market and investor pressure, MegaWeb neither assessed the suppliers employed by Ajax nor determined how closely Ajax themselves evaluated their security. By cutting these corners, MegaWeb exposed itself to both catastrophic scenarios.
So, what needs to be addressed within the M&A due diligence process to ensure neither happens to your organization?
Did Ajax Have a Third-Party Inventory?
When reviewing Ajax’s cybersecurity supply chain risk management processes, Mega Web needed to first understand what third parties they relied upon. What third parties had access or transmitted data to Ajax systems, data, and facilities? What Ajax data resided in third-party systems? Which third parties provided critical or strategic services to Ajax or interacted directly with customers?
To answer these questions with a high degree of certainty, Ajax would have needed a repository listing all third parties and their detailed interactions by the company. There would need to be documentation of the operational and reputational effects of a third-party breach, and the consequences a loss of service would have on the organization.
Had this been available, MegaWeb Corporation would have understood factions they would be inheriting as third parties; the risks each supplier presents; the risk mitigation, liability, and indemnification built into third-party contracts; and if they would want to keep those relationships, renegotiate, or terminate contracts.
Did Ajax Understand Who Their Critical Suppliers Were?
Beyond a vendor repository, MegaWeb should have ascertained Ajax knew who their critical and strategic third parties were. Understanding which ones provide business-critical and strategic services, which connect to sensitive data and systems, and which have access to internal networks is integral to an effective cyber risk management strategy. Once identified, those third parties with higher levels of access, or who provide business-critical services, can be prioritized based on urgency and security requirements for contracts and agreements.
Had MegaWeb determined whether Ajax performed these leading practices around their critical suppliers, they would have been better able to assess the level of risk posed by Ajax’s third-party suppliers prior to connecting their systems.
Did Ajax Conduct Due Diligence on Its Suppliers?
Mega Web Corporation should have determined whether Ajax examined their suppliers’ security postures and if they met a high level of expectation. A key aspect of cybersecurity supply management is conducting periodic due diligence and monitoring reviews to assess the controls that are in place over inherent risks to determine what residual risks impact the organization.
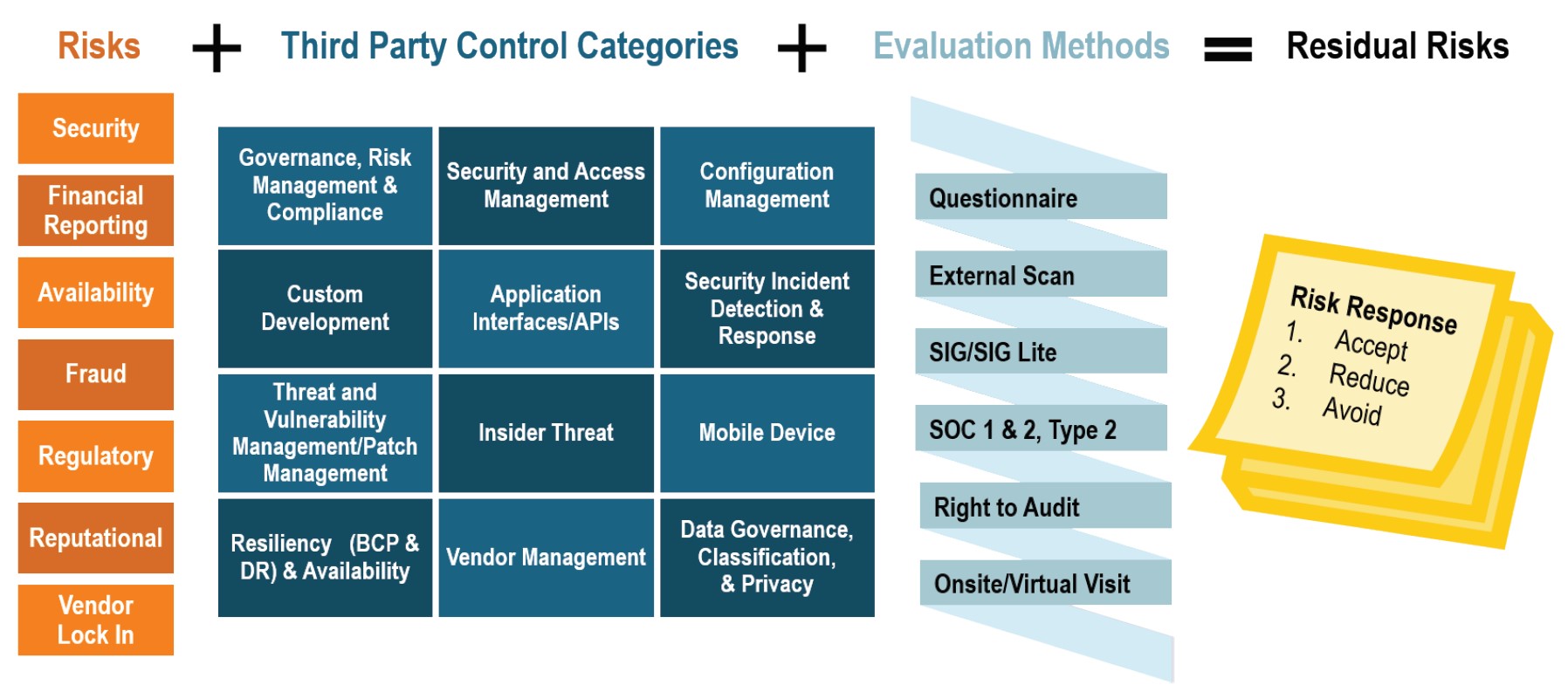
If MegaWeb had been able to determine what third parties Ajax considered risky through these types of reviews, whether the risks were potentially impactful, and what risk mitigation strategies were in place during the acquisition integration, it would have helped them to make key business decisions during the acquisition process.
Did Ajax Require Third Parties to Remediate Findings and Inadequacies?
Third-party reviews serve a critical purpose: drive down risks posed by the third parties and their services and products. During these reviews, uncover risk items the organization is not willing to accept and will need to be addressed prior to the acquisition. Best practice organizations not only conduct these reviews but also have established processes to monitor and manage identified findings, in accordance with language included in contracts with each third party.
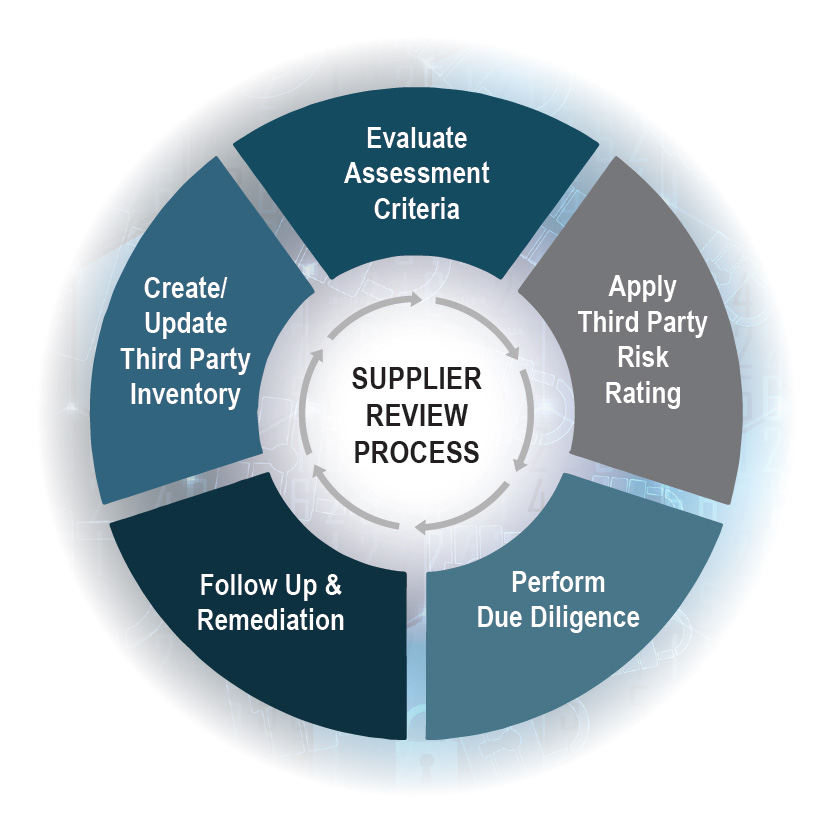
Had MegaWeb Corporation validated that Ajax was tracking remediation requirements for third parties, established remediation timelines with third parties, and ensured that they were following up on the open items until resolved, these deficiencies would have been corrected. They would have been comforted to know that Ajax demonstrated a requirement for their suppliers to meet an equally high standard of security.
How Was Ajax Leadership Informed of and Kept Aware of Third-Party Risk?
Lastly, MegaWeb should have looked at how leadership was kept informed of third-party risks and the associated consequences of a breach or loss of service.Developing Key Performance Indicators (KPIs) and dashboards on third-party risk levels would have helped to ensure that Ajax leadership had a clear picture of the third-party risk landscape, such as having quarterly executive board reporting (i.e., report out the number of transfer pricings [TPs]: new, terms, those in due diligence, key risks if any), monthly risk committee meetings, an escalation process defined to obtain appropriate approvals when risks are not adequately remediated, and review of contract terms to determine if the third-party risk was adequate (i.e., a formal risk acceptance process). Had this been the case, MegaWeb Corporation would have gained assurance of the overall effectiveness of the third-party risk management program.
Organizations can address possible internal controls, but if they are not approaching third-party risk with the same level of urgency, they are missing one of the main attack vectors we see in cybersecurity today. If MegaWeb Corporation ensured that Ajax had an effective third-party risk management program, they could have identified risky third parties that led to their compromise, made sure deficiencies were addressed, and severed ties with the third party before suffering downtime, lost revenue, and reputational damage.
Editor’s note: Updated January 2022